Spam and Phishing
The top method that cybercriminals use to gain access to your device or information is through social engineering methods.
By identifying these methods, we can ensure that we do not become victims.
Spam
Spam is unsolicited and unwanted email. Here are some tips to reduce spam:
- Report Spam: Most email clients have a built in way to report spam. By reporting spam, you also prevent this specific spam message from finding its way to your inbox again. For how to report spam on outlook, click here.
- Enable Filters: By enabling and tweaking filters, you can prevent spam from reaching your inbox and instead, they are sent to your junk folder. It is a good idea to perioridically check your junk folder to make sure only undesired emails are there. Ocassionally legitimate messages are improperly filtered.
- Be Wary: Ask yourself if entering your email on any given form is required. Hide your email on your online profiles. Change your settings to only allow certain groups of people to access information about you, including your email address.
Phishing
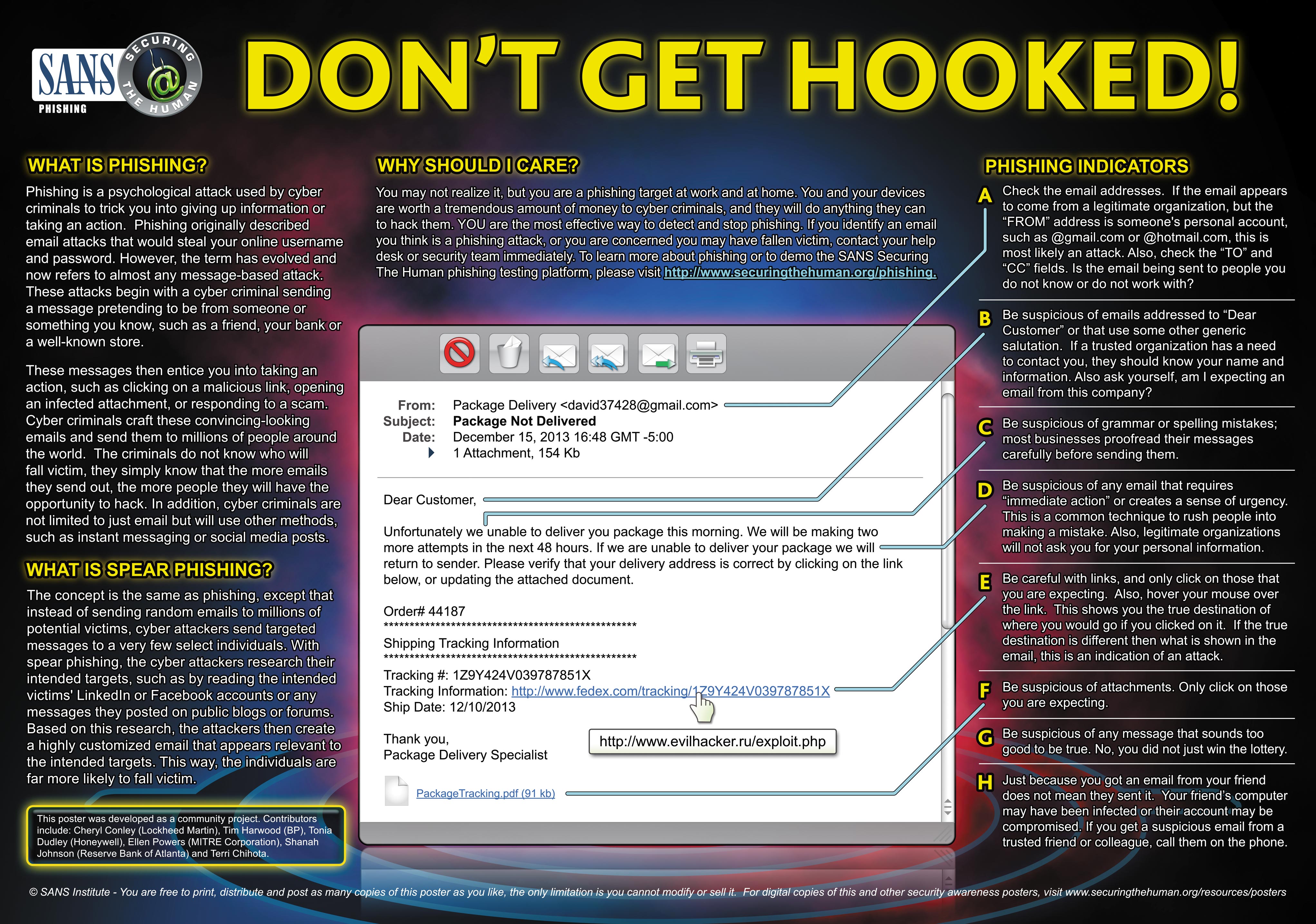
By using emails or malicious websites, cybercriminals launch phishing attacks to collect personal or financial information on you or infect your machine with malware and viruses.
Spear Phishing is an organized and directed phishing attack against a group or organization. In this sophisticated, targeted social engineering attack, cybercrimals attempt to gather credentials to gain access across that organization's network. Cybercriminals fabricate a genuine-looking email from a business or organization to lure criminals in giving up these credentials. If you suspect such a spear phishing attack against Moody, please report it using the methods in the "Contact Us" box.
Spear Phishing also extends to social media such as Facebook, Twitter, or Youtube. Select the proper link to report spear phishing attempt on these social media networks.
Secure Solutions - What You Can Do
- Questionable link/site? Don't risk it: Links, attachments, and too good to be true offers are the number one way that cybercriminals gain access to your data or machine. It is not worth the risk. Even if you know the source, delete it. It's possible that source was compromised. More information on Spam and Phishing here.
- Be aware: If a link demands your immediate attention, implores you to enter information about you or your account, or makes an offer that seems too good to be true, it likely is spam and follow the steps above to report or filter out such messages.
- Use secure passwords: The strongest password is not simply one word spelled in a difficult way with weird characters. The strongest passwords are actually passphrases that are at least 12 characters long that are unique and memorable - just to you. More information from NIST (National Institute of Standards and Technology) here. It is also advisable to use a different password for different accounts to prevent cybercriminals to gain access to all of your accounts.
- Lock down your login: Secure your accounts with available tools to add an extra layer of security. Your usernames and passwords are not enough to secure important accounts like social media, email, and banking. (While the link in this bullet point may prove helpful, this source is not at all associated with Moody Global Ministries.)
If you are a victim:
- Report it: Please let us know immediately by using the methods in the "Contact Us" box. If it is not a Moody account, contact the right organization or financial institution immediately.
- Look at the activity on your account: Watch for unauthorized charges or activity that may not be you.
- Consider reporting the attack to your local police department, and file a report with the Federal Trade Commission or the Internet Crime Complain Center.
Contact Us
You can contact the CyberSecurity team at
cybersecurity@moody.edu
In case of an emergency, contact the Support Center at (312) 329-4001.